Policy rules can be administered to detect valuable company and personal information including intellectual property, credit card numbers, and social security numbers and retrievable through a quick search function for auditing and legal evidence.
Monitor
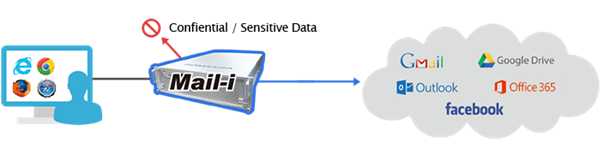
Mail-i monitors and analyzes outbound network packet and protocol traffic based on content/context policies.
- Visibility: Monitors and controls data traffic across multiple ports and network communication channels.
- Protocols: Email, Webmail, IM, FTP, Telnet, P2P, Tunnel, HTTP/HTTPS, Cloud Services including Office 365, Google Apps, AWS, iCloud, and more.
Mail-i detects sensitive data in motion including intellectual property and personal information.
- Blocks and secures bypassing & proxy-based traffic and protocols.
- Prevents sensitive data in motion based on policies.
- Policy actions include block, log, alert and more.
Management
Mail-i provides pre-defined and customizable policies based on regulatory compliance, industries.
- Central Management Console
- Create/Manage Policies
- Detailed Graphic Reports
- Real-time Alerts
- View detailed Incident Logs, Who, What, When, Where, How?
and protect confidential and customer information.”
– Jae Choi, IT Director, Center Bank
Data Visibility
Mail-i monitors and manages sensitive data traffic across multiple ports, network protocols, and channels.
Easy to use
Mail-i can be quickly and simply deployed/set-up into your network environment without alteration or performance effects.
Using Mail-i features, companies can comply with local data privacy laws and industry regulatory compliance related to electronic data and communications.
(Manufacturing)
Institution
Institution
